Wireshark (Network traffic analysis)
| F.A.Q.Wireshark is a free and open-source tool used for network traffic analysis. It is a popular program used by network administrators, security engineers, developers, and researchers for network monitoring and debugging.
Wireshark allows the capture and analysis of data packets transmitted over a computer network. It can be used for investigating and diagnosing network problems, monitoring network traffic, analyzing the performance of network applications, identifying security threats, and many other purposes.
The program supports multiple network protocols such as TCP/IP, HTTP, DNS, FTP, SSH, SSL, and many others. Wireshark enables detailed analysis of each packet, displaying information about the source and destination, protocol type, headers, and data transmitted over the network.
Additionally, Wireshark offers advanced filtering capabilities that allow for extracting and analyzing only the packets of interest. We can also save captured data to files or export analysis results in various formats.
It is important to note that Wireshark is a powerful tool that can be used for both diagnostic and illegal purposes. Therefore, it is essential to use it in a legal and compliant manner according to applicable regulations.
To conduct tests, we need a server with network access. We have servers available for ISPs on which such tests can be performed.
After launching the program for the first time, available network interfaces for analysis will appear.
After selecting the Ethernet interface on which the network traffic takes place, we move to the next window. The program will listen to everything that happens on the given interface.
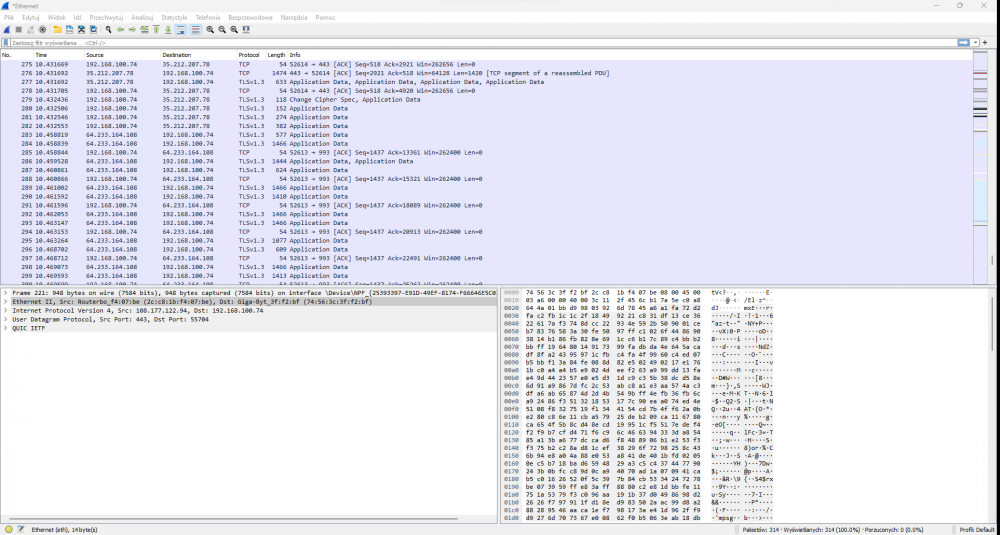
In order to search in the above logs, for example serverparts.pl sites of interest, it is necessary to add the server dns in the wireshark settings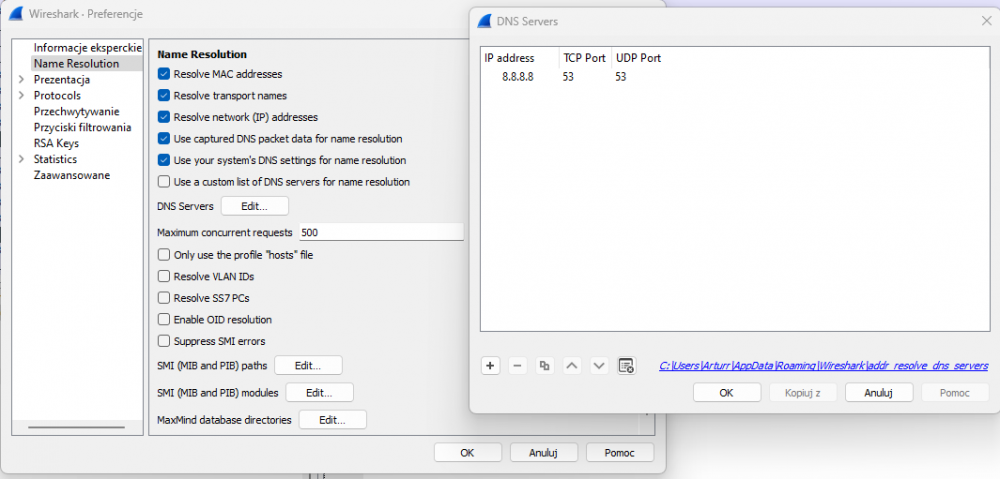
And then use the command in the filter ip.src == serverparts.pl and we should get the following filter result
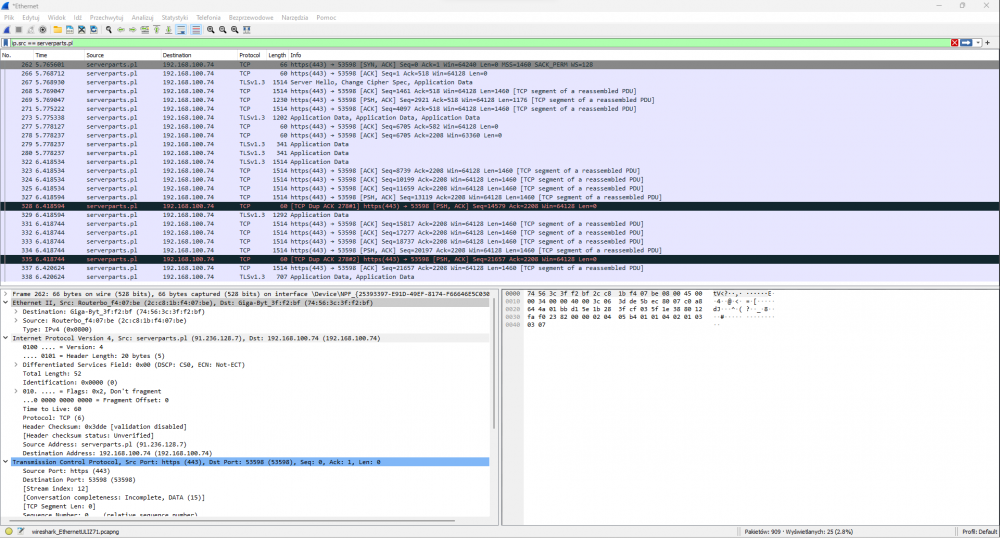
Example commands:
tcp dst port 22 Displays packets sent to TCP port 22.
ip src host 172.16.200.185 Displays packets from source address 172.16.200.185
host 10.1.2.3 Displays packets from either the source or destination address 172.16.200.185
tcp port 23 and not src host 10.0.0.5 Displays traffic on port 23 from any address except 10.0.0.5
Operators used in filtering
|
Operators |
Descriptions |
Example |
|||||
|
eq or == |
Equal |
|
|||||
|
ne or != |
is not equal to |
|
|||||
|
gt or > |
Greater than |
|
|||||
|
lt or < |
Less than |
|
|||||
Logical Operators
|
Operators |
Descriptions |
What it Returns |
||||||||
|
and or && |
AND |
All conditions should match |
||||||||
|
or or || |
OR |
All or one of the conditions should match. |
||||||||
|
xor or ^^ |
XOR |
Exclusive OR (XOR) - only one of the two conditions should be met, not both. |
||||||||
|
not or ! |
NOT(Negation) |
Not equal. |
||||||||
Related pages:

